SUCCESS CASES
Energy & Utilities
A COMPLETE AND INNOVATIVE SOLUTION FOR RISK INTELLIGENCE ACTIVITIES
The majority of the supervisory and control bodies of listed companies require companies with high exposure and a large number of private information on retail clients, very strict rules for the management of risk management processes and the safety of ICT infrastructure, in order to protect customer privacy.
THE CONTEXT
With the rise of digital information, the activity of data protection and alignment of ICT infrastructures with the company’s core processes has become a very important task; this is mainly due to the huge amount of data generated by large network infrastructures and massive exposure – especially for companies with a large number of employees – to external accesses and the need to regulate their processes and transactions according to privacy regulations and sectoral obligations.
Furthermore, events such as the violation of sensitive client data or attacks on ICT infrastructures can lead to very negative penalties and results in terms of public perception about the security and reliability of the company.

THE CLIENT

The client had a series of very powerful but all different security appliances; solutions and tools that have been added over the years to protect the various infrastructural layers and that do not integrate with each other. Therefore, the key requirements that the client demonstrated to the ESC 2 team were the following about the company’s safety and reliability:
- Given the diversity of formats, the difference in infrastructure layers and the huge number of detailed feeds and reports from ICT Security operations, the client had difficulty in putting together information at the level of detail and difficulty in creating a high-level reporting. level on the underlying risks and their trends;
- The reporting processes in the areas of Digital Information and ICT Security Management required an overall improvement in terms of uniformity and semantics of the results of the various analyzes carried out on production, in order to obtain a clear and comparable view of ICT risks.;
- It was necessary to create an aggregated reporting model for ICT risk management, which would also have made it easier to understand the changes in the nature of the attacks and incidents, and therefore the potential of the risks existing on the different dimensions and on the different layers.;
ESC 2 APPROACH
Based on client requests, the ESC 2 team proposed an integrated solution with the following key functions:
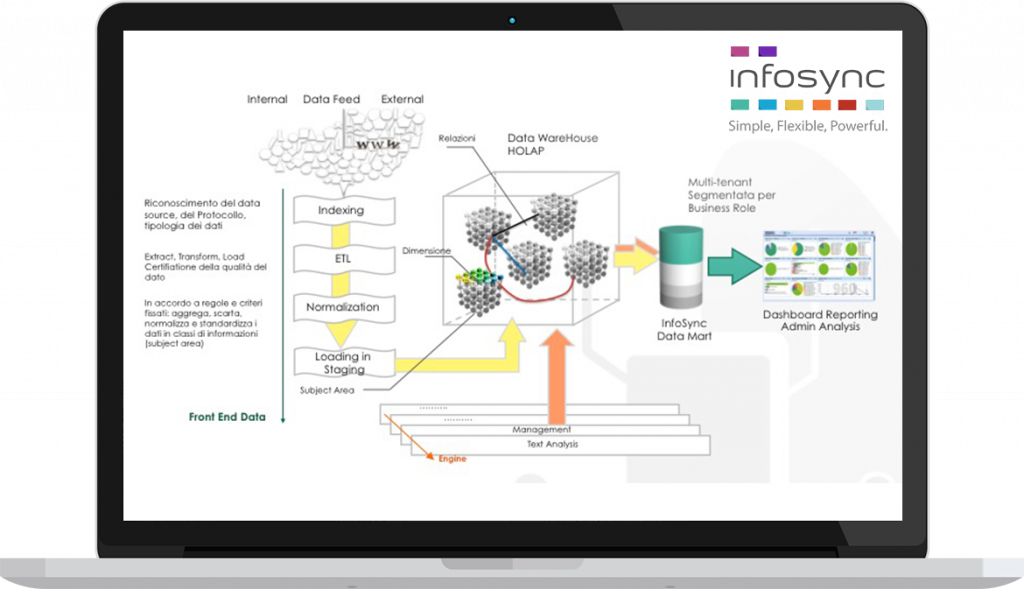
- Collection, normalization, reuse and aggregation of all the information generated by logs and reports, such as those produced by the different security appliances, creating a clear and complete basis for risk intelligence, to be used on a new framework for the analysis of risk with simple and functional dashboards and drill-down navigation schemes within processes;
- Aggregation and risk assessment based on the best practices of the COBIT and ISO 27005 sectors, creating a standardized evaluation criterion;
- Implementation of a unified view of risks on all dimensions: Business services, Department, functional areas, ICT layers and other assets;
VALUE FOR THE CLIENT

After a phase of progressive implementation of the solution which lasted about 3 months, the customer integrated the new database created on the Infosync platform and generated a series of dashboards and charts for the navigation drill-down, fully meeting the expectations of management regarding company policies, client data security and compliance.
ACHIEVED RESULTS
- Normalization and reuse of logs from different data sources;
- Standardization of the reporting model to support risk assessment processes;
- Alignment with risk assessment best practices (Cobit5, ISO 27001, Privacy Law);
- Reduction of the complexity of internal audit processes and compliance with the directives on the treatment, conservation, security and privacy of customer data;
