SUCCESS CASES
Telco
AN INTELLIGENT SOLUTION FOR THE REPORTING AND CORRELATION OF DIGITAL RISK
With the age of information digitization, ICT infrastructure protection has become a much more massive and complex activity; this is mainly due to the huge amount of data generated by the large network infrastructures together with a massive exposure – especially for companies with a large number of employees – to external accesses, with the consequent need to regulate their processes and transactions according to the regulations privacy and industry obligations.
THE CONTEXT
In the telecommunications market, events such as the violation of sensitive customer data or attacks on ICT infrastructures can lead to very negative penalties and results in terms of public perception about the security and reliability of the company. All of these issues today have made IT risk protection a crucial and necessary process to protect the company from reputational risks.

THE CLIENT

The client is one of the top three Italian mobile and fixed-line operators by capitalization, number of customers and global reach. With a large retail presence throughout the country, it is part of one of the ten largest telephony groups in the world.
CLIENT NEEDS:
The client had a very complex ICT infrastructure, with all sorts of solutions, appliances and security tools, added over the years to preserve different levels of infrastructure and regulate compliance processes. In accordance with it, the needs that the client showed to the Esc2 team were as follows:
- Given the dissimilarity of formats, the difference in infrastructural layers and the huge number of detailed feeds and reports from ICT Security operations, the client has had many difficulties in gathering information at the level of detail and, vice versa, in creating high level reports on the underlying risks and their trends.
- The client therefore required the creation of an aggregated reporting model for ICT risk management, which would also make it easier to understand the changes in the nature of the attacks and incidents, and therefore the potential of the risks existing on the various ICTs and on the different layers;
- The client also needed to integrate compliance for the PCI-DSS standards in order to be authorized by local financial regulators to enable payments through the main international circuits. This entailed the implementation of additional security measures for all infrastructure levels, for all applications that processed sensitive customer data and, given the nature of the information, to ensure compliance with local and international privacy laws;
- Since the holding company is listed on the NASDAQ list, the companies in the group were also subject to compliance with the Sarbanes-Oxley-Act regarding corporate responsibility. The client therefore needed to standardize the common framework locally and internationally, based on standard guidelines such as ISO 27001;
ESC 2 APPROACH
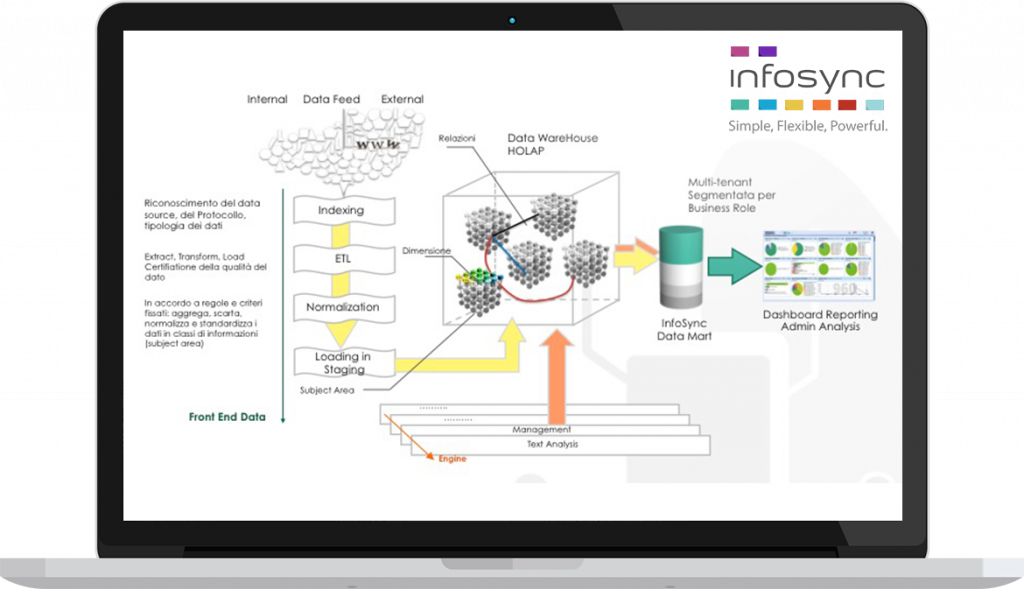
- Collection, normalization, reuse and aggregation of all the information generated by logs and reports – such as those produced by the different security appliances – in order to create a clear and complete basis for risk intelligence, to be used on a platform with a semantic alignment integrated on different layers of data warehouse security and dimensions and a simple and intuitive front-end, with user-created dashboards and drill-down exploration possibilities;
- Aggregation and risk assessment based on industry best practices: COBIT 5 (with regard to business processes) and ISO 27005 (for technology chain);
- Implementation of a unified view of risks on all dimensions: business service, department, functional areas, ICT layer and assets;
- Flexible libraries to support the compliance imposed by the PCI DSS, SOX and Privacy standards at multiple levels;
THE RESULTS ACHIEVED

After an implementation divided into two major phases, with a total duration of approximately 9 months, the client gradually integrated the new database for the Infosync RM platform and generated a series of dashboards and charts for the navigation drill-down, fully meeting the management’s expectations regarding compliance, company policies and security reporting.
THE ADVANTAGES
- Normalization and reuse of logs from different data sources;
- Standardization of the reporting model to support risk assessment processes;
- Alignment with risk assessment best practices (Cobit5, ISO 27001, Privacy Law);
- Improvement of internal audit processes on all relevant aspects of ICT security and monitoring of compliance levels on all the different directives and regulations;
