IDENTITY GOVERNANCE
A NEW METHOD FOR ACCESS REGULATION
THE IAM SYSTEM OF ESC 2
We know how important it is to protect companies’s information assets and the need to have control and an integrated view on “who accesses what”, especially in contexts with a high number of users.
This is why we offer customized solutions for the installation of systems for Identity Access Management.
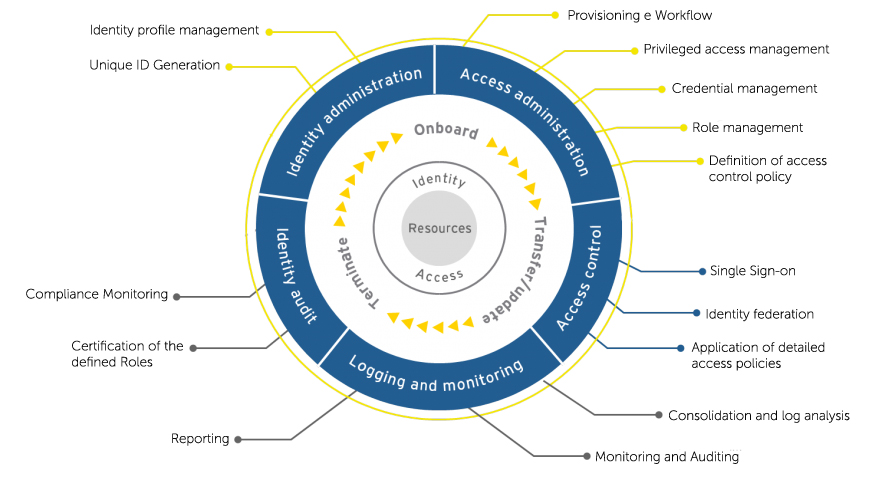
1
2
3
4
5
Safe and fast access
Grant access quickly and safely through authorization workflow, assignment of role-based access rights and automated provisioning / deprovisioning and single-sign-on (SSO) functionality.
Simplified control
Reduce complexity in identity management by integrating multiple identity repositories into one framework to eliminate multiple IDs, duplicate passwords and orphaned accounts.
Authorizations management
Reduction of profiles and change of the authorization model. RBAC model implementation – matrix of job roles issued by BU Profiling Managers and SoD checks.
IT administration costs control
Provisioning/deprovisioning automation in terms of employee job title, location and business unit ID, implementation of user utilities, reduction of reconciliation and control effort.
Monitoring and auditing
Periodic certification of the subsistence of the assigned roles, of the grants established for each role, consistency check between credentials on the target and flows authorized by the IAM platform.
